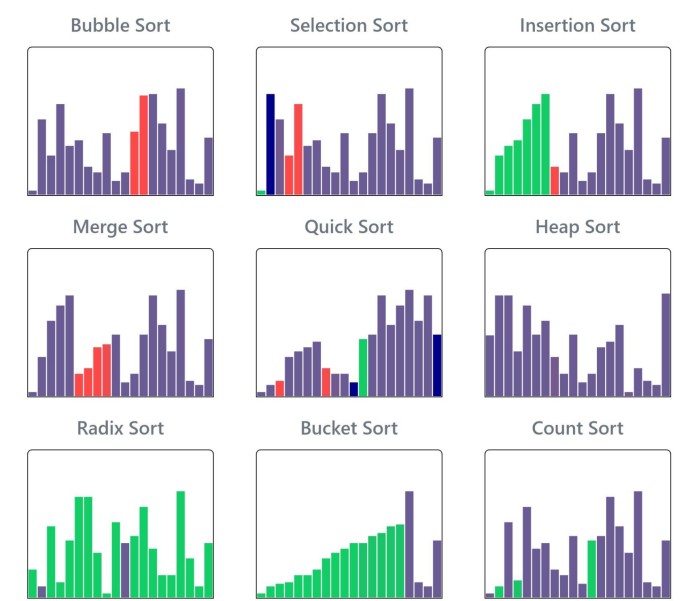
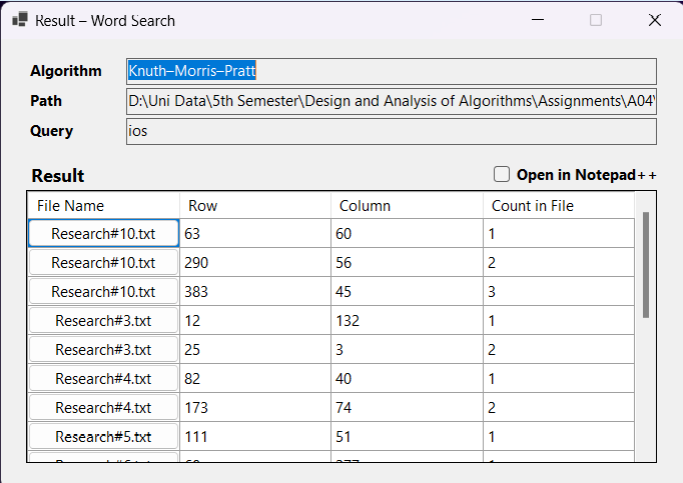
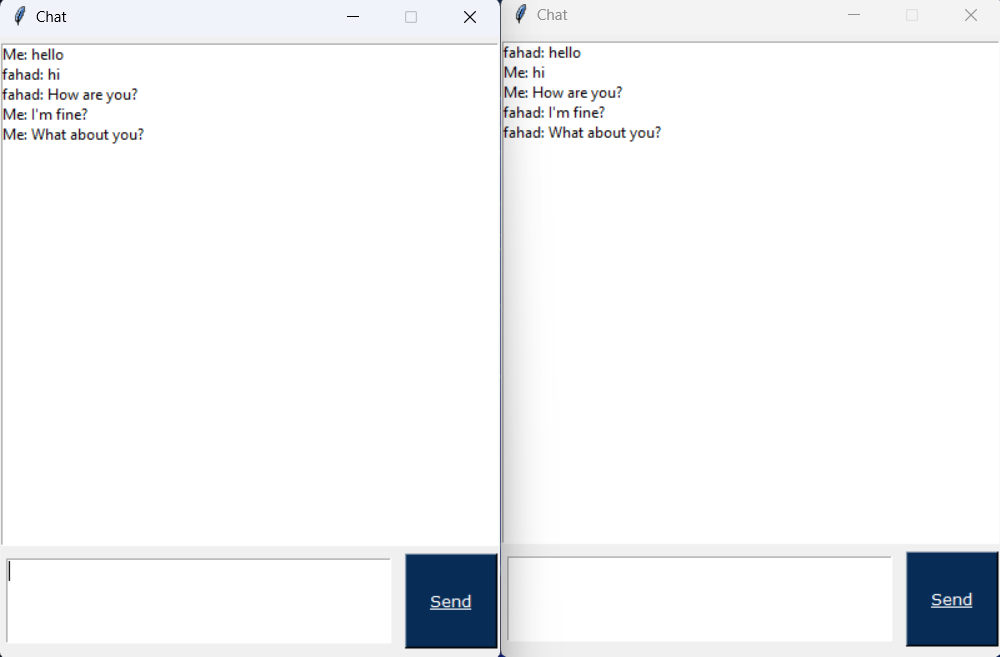
About Me
As a Cybersecurity and Digital Forensics student, I am passionate about protecting against digital threats and uncovering the truth through digital investigations. My interests lie in various aspects of the field, including Cybersecurity, Digital Forensics, and Software Engineering. With a solid foundation in these areas, I am ready to make a meaningful impact on the industry and help keep our digital world secure. My ultimate goal is to become a leader in the field and leverage my skills to tackle complex cybersecurity and digital forensics challenges. Additionally, I'm an enthusiastic and detail-oriented individual who enjoys problem-solving and exploring new ideas. I firmly believe in building upon existing solutions and refining their underlying systems, rather than reinventing the wheel. It's similar to focusing on the bearings, chassis, and engine-block, rather than building the entire car from scratch.
Skills
- Web-Application Pentesting
- Vulnerability Assessment
- Digital Forensics
- Malware Analysis
- Shell Scripting
- Python
- C/C++
- Golang
- HTML/CSS/JS
- MERN Stack
- ELK Stack
- NextJS
- Data Scraping
- IAM
- ForgeRock
- OAuth
- OIDC
- SAML
- Cloud Computing: Azure/AWS
- Devops: Docker, Jenkins